It is my belief that, to protect yourself online, consumers should not use an Internet connection via Ethernet cable and WiFi (free or per pay) without having a virtual private network (VPN) running at the same time. The era of hopping from free WiFi to free WiFi without a VPN is absolutely over.
This post is written with the not-so-techie reader in mind. If you’d like to go further into the ultra-technical details on how a VPN works, there are plenty of other sources of information on the topic.
What Is A Virtual Private Network?
Imagine you have a virtual pipe running parallel to your Internet connection. In technical terms, we call this tunneling. This pipe has a different Internet Protocol (IP) address than your regular Internet connection, and the connection through this tunneling (pipe) is encrypted. It does not matter who provides you with Internet services, you can always add a VPN service on top of that for your computer, phones and tablets.
How Does a VPN Work?
You first connect to the Internet but your computer does not access the actual Internet until your VPN has engaged (if you use ExpressVPN.com with this option selected – highly recommended). Thus, you are using the public telecommunication infrastructure (Internet) but with an encrypted layer of protection that will not allow anybody to snoop on what you are doing while surfing the Internet.
Why Do I Need A VPN?
Every time you visit a website, the webmaster can see your visit because you are disclosing your actual IP address. Your Internet provider can see the sites you are visiting too. Even though you might not be visiting websites that are considered compromising, your privacy is the precursor of security. Thus, when all the companies are creating a profile of your Internet habits, your privacy ends up being the product they sell to whomever is willing to pay most. These buyers are marketers and also crooks.
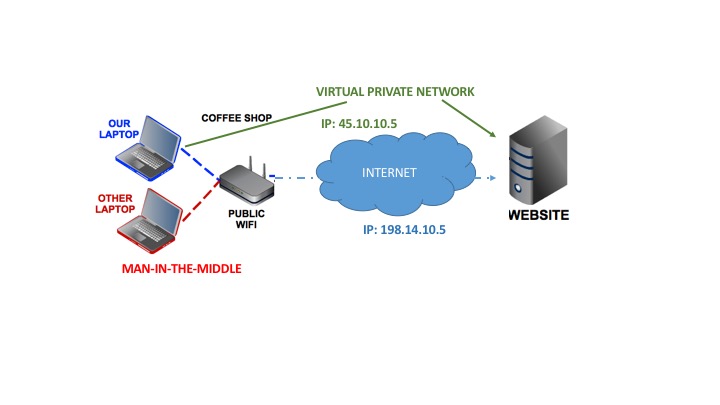
The illustration below shows how you can be using your laptop (phones or tablets, too) at a coffee shop, hotel, airport or even your own home, to view websites with a blue – non-encrypted connection and the red laptop along with the website master can see everything you do. On top of the illustration, you see how your IP address changes when you use an encrypted connection to look at the same website and the man-in-the-middle can no longer jump into your connection.
At home, you are probably embracing the phenomenon of the Internet of Things (IoT). You have many devices connected to your network, including cameras. When these cameras are not running on an encrypted tunnel (VPN), they can be accessed by anybody. Do you want to have fun? Take a look at Insecam.org. This website shows all unsecured cameras in the world. Do you want your camera to be listed in this website too? If your answer is no, then begin by changing the default passwords on all the devices you connect to the Internet and ALWAYS use a VPN.
What Are the Best VPN Services?
Any VPN company offering their services for free has made you the product by selling your private information. Encryption is very expensive, and we do not want anything lower than AES256. Thus, you need to expect to pay between $8.25 to $8.35 per month for a good VPN.
ExpressVPN.com has been voted by many reputable organizations as the best service provider, and it is the one I highly recommend. Other well-rated companies are Buffered, IPVanish, NordVPN, and VPNArea. You can read a well-written comparison on BestVPN.com.
How Do I Configure A VPN? Can A VPN Be Used On Multiple Devices?
Should you decide to go with my recommendation of ExpressVPN.com, you can have one account that includes one computer, one phone and one tablet. The computer can use the same account at the same time as the phone or the tablet; but the phone and the tablet cannot share the same account at the same time.
To configure your VPN, go to Preferences, and ensure that you put a check mark on the two options under Network Lock. Under Protocol, select Automatic. Under Advanced, remove the check mark for the Diagnostic Data. In your smartphones and tablets, make sure you select to Auto-reconnect, and that the Share Diagnostic Data is off.
 Cecilia Anastos holds a Master’s Degree in Strategic Intelligence w/sp in Middle East Issues, a Graduate Certificate in Cybercrime, and a B.A. in Criminal Justice w/sp in Psychology. In 2005, Ms. Anastos founded Meta Enterprises, LLC (Meta-Intelligence.com) where she works as Chief Intel Analyst – OSINT, Business/Competitive, Cybercrime and Instructor. Fluent in five languages, she is a pioneer in the utilization of digitized open source and publicly available information to create actionable intelligence, and in the reduction of digital signatures in the cyberspace domain; and has designed many of the cyber programs currently used at the US Navy Special Operation Forces, police departments, and private sector. In 2016, she was recognized as one of the most influential business leaders in the field of cybersecurity by the SDBJ500. Connect with Cecilia on Twitter @meta_Int3l.
Cecilia Anastos holds a Master’s Degree in Strategic Intelligence w/sp in Middle East Issues, a Graduate Certificate in Cybercrime, and a B.A. in Criminal Justice w/sp in Psychology. In 2005, Ms. Anastos founded Meta Enterprises, LLC (Meta-Intelligence.com) where she works as Chief Intel Analyst – OSINT, Business/Competitive, Cybercrime and Instructor. Fluent in five languages, she is a pioneer in the utilization of digitized open source and publicly available information to create actionable intelligence, and in the reduction of digital signatures in the cyberspace domain; and has designed many of the cyber programs currently used at the US Navy Special Operation Forces, police departments, and private sector. In 2016, she was recognized as one of the most influential business leaders in the field of cybersecurity by the SDBJ500. Connect with Cecilia on Twitter @meta_Int3l.
Meta Intelligence brings the courses Risk Management When Online and Open Source Intelligence (OSINT) Collection and Analysis to your organization regardless of where you are located. Watch this short clip below and call us to schedule training for your team or organization.






